Malware continues to evolve at a rapid pace, constantly finding new ways to infect systems and evade detection. I often liken it to trying to catch a moving train while already lagging behind. In this report, I present my findings and efforts to analyze, mitigate, and prevent future attacks.
Hiding in Plain sight; New Vulnerability
Some of the most intriguing types of malware hide in plain sight by leveraging the GUI. For instance, APIs may be abused to verify desktop wallpapers or determine the number of connected monitors. These methods are cleverly designed to evade automated sandboxes by identifying the templated environments they rely on. Combined with other evasion mechanisms, like detecting environment artifacts, analyzing memory space, or checking for the number of installed applications, this approach becomes even more effective.
What’s particularly fascinating about these GUI-based strategies is their unconventional, almost steganographic nature. While it may be a stretch to compare them directly to steganography, the essence is there: hiding malicious intent in seemingly benign operations. Techniques such as font abuse take this to another level, allowing attackers to exploit common fonts, colors, and visual elements to stay under the radar.
How Does it Work?
At its core, this evasion technique revolves around enumerating font types (e.g., Gothic, Sans Serif, Helv) and characteristics (e.g., color, size) to prevent execution under specific conditions. The process relies on functions like SetTextColor, EnumFontFamiliesA, and SetBkColor. These functions pass parameters that the malware uses to analyze its runtime environment.
For example, EnumFontFamiliesA takes several parameters, with one key parameter specifying the font type to search for. Figure 1 demonstrates this function in action, as observed in x32dbg
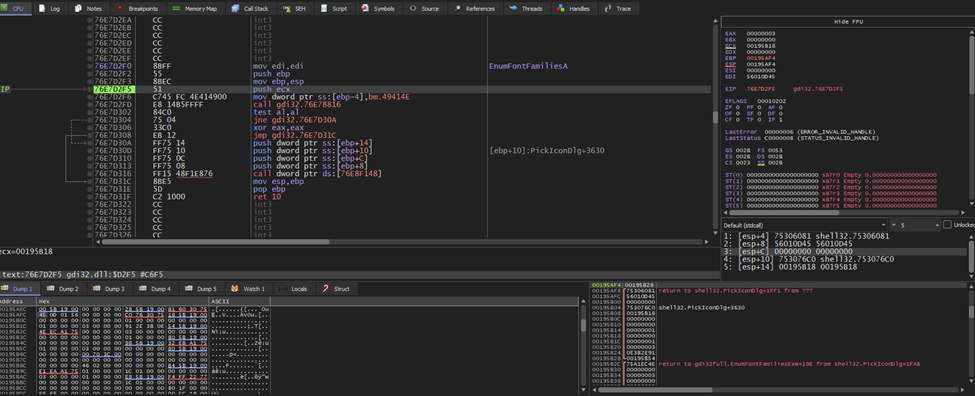
Figure 1 EnumFontFamiliesA Usage in x32dbg
Another related function, EnumFontFamiliesExW, adds even more granularity to this approach. Figure 2 highlights its use in enumerating the Gothic font type, visible in the first PUSH instruction. Comments and notes have been added to the figure to make the flow easier to follow.
We also have another EnumerationFontFamiliesExW in Figure 2, but this specifically outlines the technique of enumerating for Gothic Font type as noted on the first PUSH instruction of the screenshot (I’ve left the commenting/notes feature enabled in order to easier follow the flow).
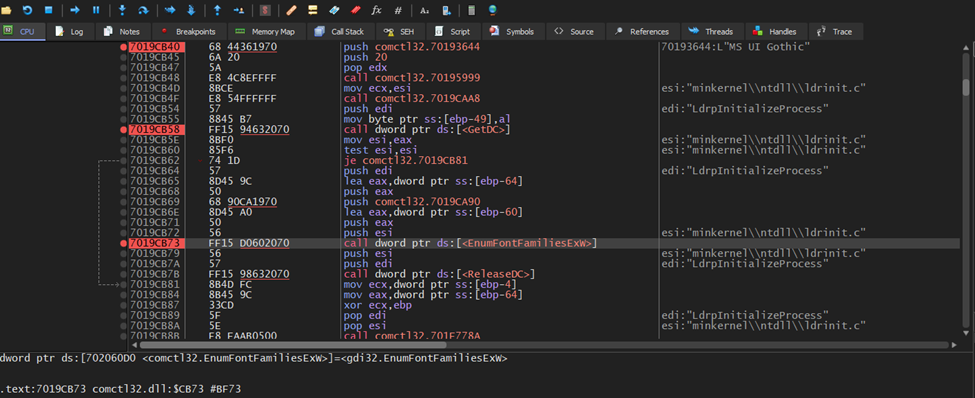
Figure 2
A targeted purpose; language evasion
One particularly interesting finding from this technique is its potential use in language-based evasion. For example, Chinese typography relies on specific fonts like simhei.ttf to render characters properly. This opens the door for malware to target or avoid detonation based on the language settings of the victim machine.
Threat actors have been known to design malware that detonates only under specific language conditions. Chinese APT groups, for instance, often program malware to activate when the system language is English but avoid activation if the language is Russian, Chinese, or Korean. Figure 3 provides an example of this type of evasion in action.
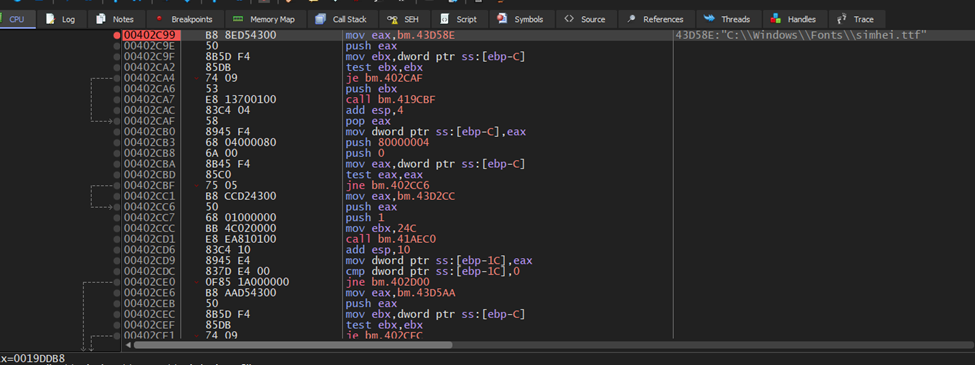
Figure 3
Future outlook
This technique has the potential to pave the way for more targeted attacks, particularly by APT groups and state-sponsored actors. The sophistication required to implement GUI-based enumeration, leveraging APIs to analyze font types, sizes, and colors, highlights the advanced knowledge of operating systems that these threat actors possess.
Font abuse represents a subtle yet highly effective method of evasion. Its creativity underscores a critical point: nothing is off-limits when it comes to exploitation in the digital realm.
NOTE: For a deeper dive into how malware combines these techniques with others, refer to my upcoming report on “BM.exe: GUI Exploitation Techniques.”


